Getting hacked is without a doubt a disaster for any organisation! One of the easiest ways to get through your organisations IT defences is to simply ask some employees for their login details… The act of impersonating a legitimate organisation and asking for details such as username passwords is commonly known as phishing.
Phishing attempts are very common because they work. Some attempts are really realistic and would likely trick most of us into giving out personal information without even realising. The good thing about phishing is that it requires you to action it. If we are careful and know what to look for we can prevent these attacks, however, all it takes is one stressed employee that blindly clicks on a link to grant access to your organisation’s sensitive data.
Here are TimberSmart’s tips that your organisation should consider in order to keep your IT system safe.
1. Go phishing
The best way to prevent phishing is to create phishing awareness within your organisation. Send safe-simulated hacking attempts to your fellow co-workers. This not only points out what users need to be aware of but also raises awareness about the reality of the attacks.
It’s so easy to send out a simulated test to your organisation to see how they do. Here is how you do it:
Check out KnowBe4 they provide a safe Phishing simulator test for your organisation with predesigned templates to use along with a report to see how everyone did during the test.
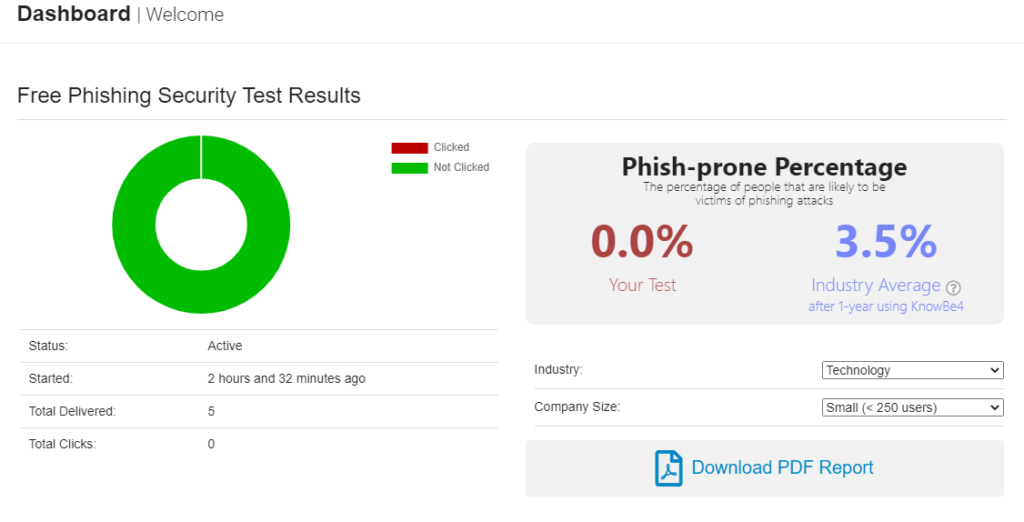
We ran through a few simple simulated phishing e-mails at TimberSmart, we were pleasantly surprised at the amount of awareness a simple test like this created amongst our employees. The ‘Phishing Security Test’ is a great way to promote awareness with an example and provides a tracked report of how vulnerable your organisation is.
For more information on how to set this test up have a look at these instructions. You will need about half an hour to prepare it and load the e-mail addresses that you would like to include in the test.
Here is TimberSmart’s trial test sent out to some of our staff members.
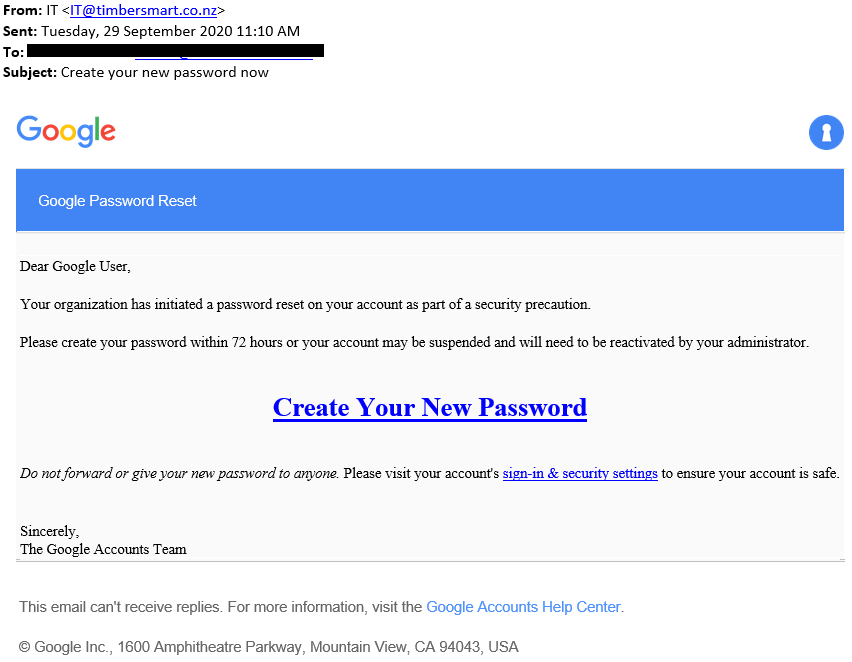
We then had access to a dashboard to summarise the response from the subjects of the test:
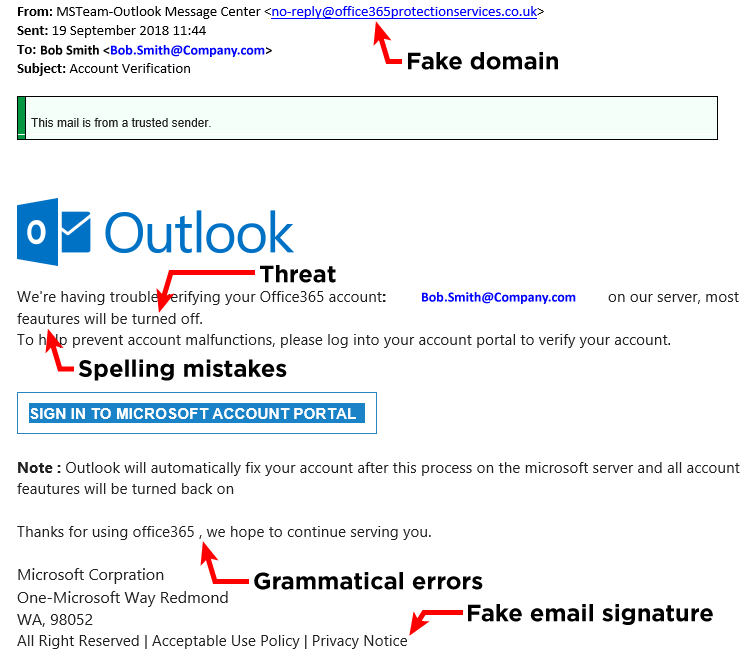
2. look for mistakes
Look for spelling and grammar mistakes. You won’t believe how many noticeable errors are generally packed into phishing attempts.
For example:
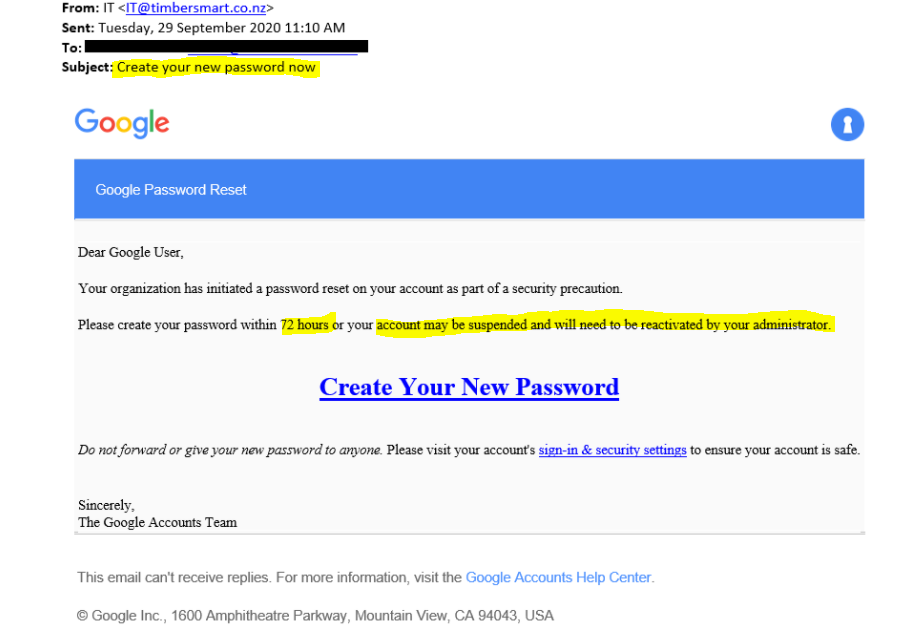
3. Be suspicious of instant action required
Be suspicious if the e-mail is requiring you to take instant action. Commonly this is sent in the form of some ‘serious security breach’, in an attempt to get you to enter your current details while ‘updating’ your password. Take threats within the e-mail as a red flag to try to get you to perform the task.
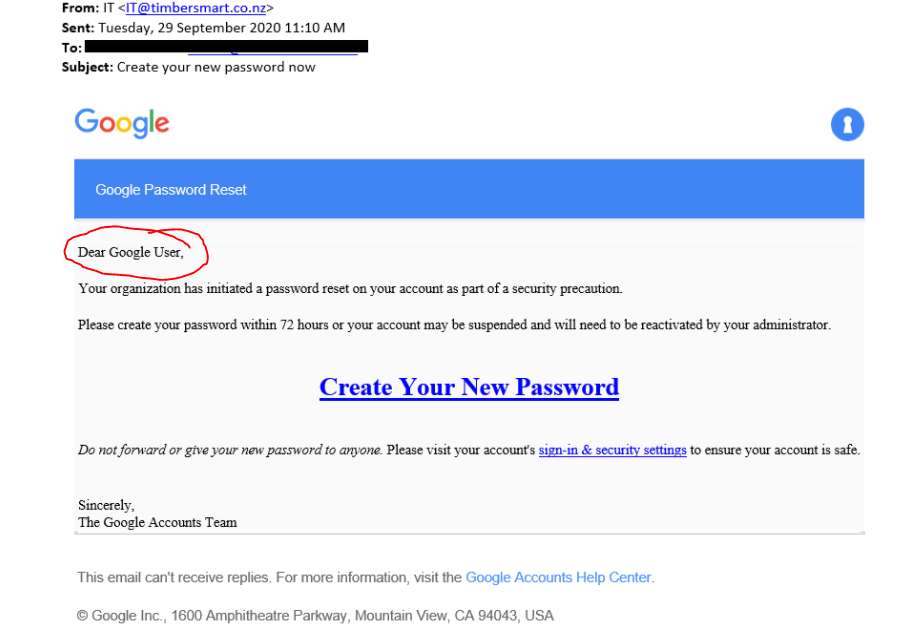
4. look for personalisation
Your trusted accounts know who you are, mass e-mail phishing attempts don’t know your name, so they use generalised greetings that can be applied to everyone. Your bank or organisations you have an account with will address you by name.
5. Use multiple lines of communication between colleagues
Just because you know the person that you get an e-mail or message from doesn’t mean its legitimate. Hackers can obtain access to their accounts and send scams from there. We are more likely to trust instructions sent from e-mail addresses we know and people we trust.
If you get a dodgy message from someone you know, Check with the person through another communication medium. A common scam is sending a phishing e-mail from an account that has been compromised suggesting that you have been sent a secure document from that person (who you know) and that you need to log in to view it. Most people simply try to log in to view the document your co-worker has sent you. Once you enter your login details you will quickly realise you have fallen victim to the trap as nothing will happen. If you notice this at this stage, your best course of action is to change your passwords as fast as you can.
6. use a password manager
A strong password is important; some sites force unique constraints on us that your one password for all generally doesn’t fit. Who are we kidding how are we supposed to remember 50 unique passwords… it’s so easy! Use a password manager and let them automatically generate a strong password for all your login needs.
7. use the wrong password
Let’s be honest sometimes even legitimate e-mails can look a bit dodgy. If you have followed all the steps and still don’t know if it’s the real deal, As a last resort, if you follow the link to log into something or confirm your credentials use the wrong password! If the page accepts the password then it’s a scam.
Fake pages do not know what your original password is, so they can’t verify if it is correct or not. If it tells you, “you have entered the password incorrectly” then you know there is some sort of verification process in the background likely to be the real site.






